More than 75% of knowledge workers are nowadays full- or parttime operating from home, while 70% of them also use private devices with unknown security status for work. What correlation is there with the massive growth of succeeded Ransome attacks – and what can you do to stop it ?
Digitalization, but even more the Covid-19 pandemic have changed how and where we work. With the vast increase of people working from home, IT had to loosen remote access restrictions (devices, users, data and systems they access) more than ever before. About 30% of the users share their device frequently with members in the same household or access online games, streaming and ‘other’ potentially malicious web sites. A shocking 26% even admit storing copies of valuable corporate data on the device in case something ‘goes wrong’ with their job. Considering the variety and count of users working remotely, we can safely assume that ALMOST ALL your valuable corporate data is somewhere ‘out there’.
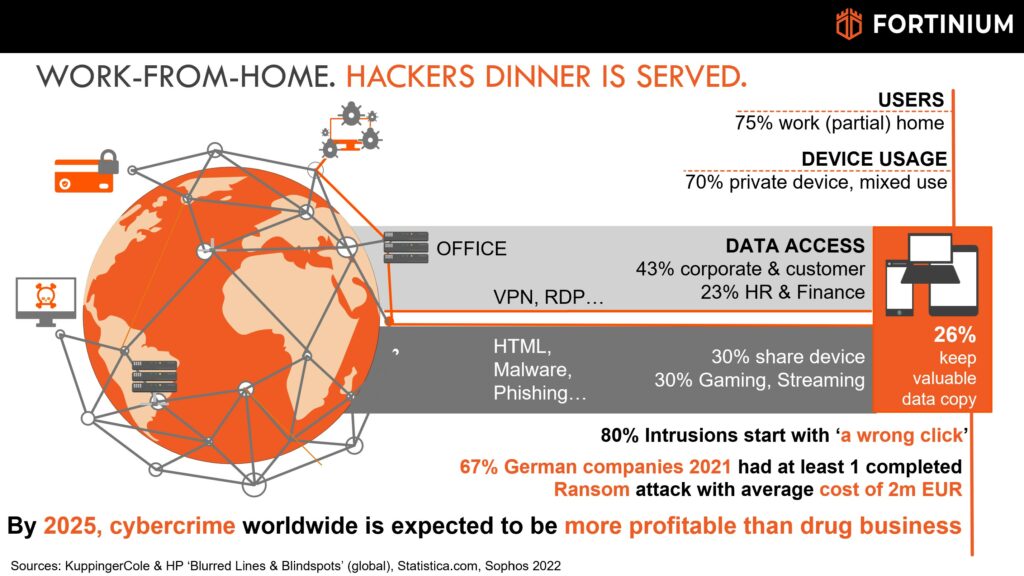
In a nutshell: There are ‘millions’ of additional, weakly secured devices on home networks, loaded with valuable corporate data and often connected to the company using VPN. The lack of discipline of users makes these devices highly vulnerable – HACKERS DINNER IS SERVED.
Stealing information to resell has become serious business. Attacking millions of devices using ransomware rather than finding that one vulnerability by hacking is far more efficient. Someone will always make that “wrong click”. Once an attack succeeded – hackers may get access to data stored locally, your identity and even the VPN connection to your company.
Not surprising that Hackers are taking advantage of our ‘new way of work’. Malware injected in Game Sites, Porn and Streaming is up by 283% and 67% of German companies had in 2021 at least one completed Ransome attack – causing an average damage of 2m EUR each.
Reactive security measures such as Antivirus products on each device and eMail scanning are a traditional and efficient method of protection, but to keep up with the fast changing patterns of malware we also need to reduce Attack Surface as well as Attack Efficiency to really regain control.
Attack Efficiency
Hackers want to get data. Avoiding to have local data and avoiding to use VPN means that any hack will not give them what they want and make the business less attractive. As a side effect – reduction of VPN usage is also a direct cost reduction.
Attack Surface
As explained above direct hacking of a machine via vulnerabilities is inefficient. The most effective way is delivering a malicious active payload, embedded in a Website that is accessed by the hackers ‘audience’. The best existing solution approach for this is using Browser Isolation (e.g. Fortinium which also can eliminate VPN) as it sandboxes each browser session and with that isolates potentially malicious code from your device and data.
